Electronic Know Your Customer
In our efforts to align our development of solutions in line with NPCI directive, Functionalities and Features, we are also offering a Veracious E-KYC System, which will enable us to provide solutions to a major part of the spectrum of banking requirements.
The following process can be applied as a Teller based solution:
• Customer reaches the respective bank to open a bank account with his AADHAR card.
• The bank receives the customer’s request and receives the signed consent form to ensure that only with the customer’s consent the information is pulled from UIDAI.
• We provide a unique facility wherein, without the consent form we will not able to proceed further to access the data from UIDIAI, also we provide an efficient document management capability wherein the request for every Aadhar detail from UIDIAI is monitored and the corresponding Consent form is accounted for and stored electronically.
• The verification of the individual’s identity is completed by authenticating the fingerprint of the individual through a biometric scanner.
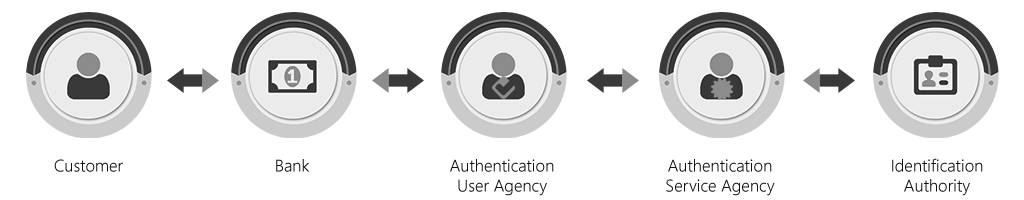
• Here in the above case as the bank can’t directly communicate to UIDAI, AUA and ASA are involved.
• Bank will send the request to AUA. AUA is any government / public / private legal agency registered in India that seeks to use Aadhaar authentication for its services. An AUA is the principal agency that sends authentication requests to enable its services / business functions.
• An AUA connects to the UIDAI [CIDR] through an ASA (either by becoming ASA on its own or contracting services of an existing ASA). In this case GSS plays the role of an AUA. We can also use the existing AUA capability of the bank.
• ASA is any entity that transmits authentication requests to the UIDAI [CIDR] on behalf of one or more AUAs. They play the role of enablement as intermediaries. They have an established secure connection with the UIDAI [CIDR] and convey AUAs' authentication requests to the UIDAI [CIDR]. ASA receive UIDAI’s [CIDR] response and transmits the same back to the AUA. In this case NPCI plays the role of an ASA. The following workflow takes place in such a scenario,
 Biometric Verification
Biometric Verification
• We scan the fingerprint of the customer using a biometric scanner.
• Once the consent form has been submitted, we send the fingerprint data and the Aadhar number to UIDIA.
• The fingerprint of the customer is verified at UIDIA and the verification result is provided to our system.
• On a successful verification the relevant AADHAR Data from UIDIA is retrieved instantaneously.
• This data received is used for further processing in Account Opening or for any other application processing.
• GSS provides the biometric scanners required for Authentication.
 One Time Password (OTP) Verification
One Time Password (OTP) Verification
• In this method of verification, as soon as the consent form is received by the bank, the bank sends the customers Aadhar number to UIDAI, upon receiving a request UIDIAI generates an OTP and sends it to the mobile number linked to the mentioned AADHAR number. Once the customer submits the received OTP to the bank the verification is complete. The bank can proceed with the verified data for Application processing.
• This data received can be used for further processing in Account Opening or for any other application processing
 FUNCTIONALITIES AND FEATURES
FUNCTIONALITIES AND FEATURES
GSS as an AUA provides the ability to use its product both as a service model – cloud based offering and as a browser based –thin client offering.
• Paperless:
The service is fully electronic, and document management can be reduced to the least.
• Consent based:
The AADHAR data can only be provided upon authorization by the customer through Aadhaar authentication, thus protecting customer’s privacy.
• Eliminates Document Forgery:
Elimination of photocopies of various documents that are currently stored in premises of various stakeholders thereby reduces the risk of identity fraud and protects the customer’s identity. In addition, since the e-KYC data is provided directly by UIDAI, there is no risk of forged documents.
• Inclusive:
The fully paperless, electronic, low-cost aspects of e-KYC make it more inclusive, enabling financial inclusion.
• Secure and compliant with the IT Act:
Both end-points of the data transfer are secured through the use of encryption and digital signature as per the Information Technology Act, 2000 making e-KYC document legally equivalent to paper documents. In addition, the use of encryption and digital signature ensures that no unauthorized parties in the middle can tamper or steal the data.
• Non-Repudiable:
The use of Government authenticated information and stored by a Government agency makes the information provided non-repudiable by the stake holders involved. Also, the use of digital signatures at both ends also makes the entire process more secure.
• Low cost:
Elimination of paper verification, movement, and storage reduces the cost of KYC to a fraction of what it is today;
• Instantaneous:
The service is fully automated, and KYC data is furnished in real-time, without any manual intervention;
• Machine Readable:
Digitally signed electronic KYC data provided by UIDAI is machine readable, making it possible for the service provider to directly store it as the customer record in their database for purposes of service, audit, etc. without human intervention making the process low cost and error free; and
• Regulation friendly:
The service providers can provide a portal to the Ministry/Regulator for auditing all e-KYC requests.
• Ease of Use:
This methodology makes the entire process of authentication and processing an application the easiest possible.